I regularly write about fraudulent aspects of finance, and it’s getting worse.
As I say in my presentations: “with five billion points of data breach, how can you keep secure?” and this is a key question, as every mobile device is now a point of payment or sale.
Equally, as everyone is loosely leaking their private information online socially, can anything remain secret?
It seems not in the age of Wikileaks, Twitter and Facebook.
Now most of the headlines about fraud are grabbed by Sophos in my circle of radar.
I guess it’s because they’re pretty good at monitoring this stuff and capturing the headlines before anyone else.
But I did see a couple of other interesting reports used recently.
One came from Guardian Analytics, whose “2011 Business Banking Trust Study” found the following:
- Fraud Attack Rate: 56% of businesses reported experiencing payments fraud or attempted payments fraud in the last 12 months. 75% of businesses have experienced account takeover and fraud in the online channel. These rates are the same as they were in 2010, indicating banks and businesses are struggling to make progress on the issue.
- Fraud Detection Rate: In 78% of fraud cases, banks failed to catch fraud involving the illegal transfer of funds or other nefarious practices such as information identity theft.
- Responsibility and Liability: 41% of respondents said that in their opinion, the bank would not cover any losses if their company’s bank assets were stolen and not recovered. This perception increased from 26% in 2010. Despite this increased awareness, 70% of businesses still feel that their institution should be ultimately responsible for securing online accounts.
- Customer Churn: 43% of businesses said they have moved their banking activities elsewhere after a fraud incident. 10%of businesses that have experienced fraud have terminated their banking relationship following fraud attacks, and additional 33% said they did not fully terminate their relationship, but moved their primary cash management services to another institution.
The key line for me from the above is “43% of businesses said they have moved their banking activities elsewhere after a fraud incident” … it’s probably higher for consumers as moving a business account is actually more challenging than moving a personal account.
You need to move all your supplier and customer data across and you no doubt have some form of relationship with the bank. This may be a relationship of some depth if the business has factoring, invoicing, treasury, cash management and other matters handled by the bank.
So for more than two out of five firms to leave if fraud occurs is a substantial exposure.
And such exposures are becoming more often and more frequent. For example:
“The FBI said that between March 2010 and April 2011, it identified twenty incidents in which small to mid-sized organizations had fraudulent wire transfers to China after their online banking credentials were stolen by malicious software.”
Small beans today … big trees tomorrow … especially when you see stories like the one I told recently about Aaron Barr, Head of Cybersecurity for the Federal Division of HBGary who got cyberpwned by the @Anonymous twitter group.
Perhaps, even more interesting, is that many of the presentations I’ve seen recently have been referring to the Verizon “2011 Data Breach Investigations Report”.
Why?
Because of this key paragraph from page four:
“We are often asked whether “the Cloud” factors into many of the breaches we investigate. The question is both easy and difficult to answer. The easy answer is ‘No—not really . We have yet to see a breach involving a successful exploit of a hypervisor allowing an attacker to jump across virtual machines (VMs), for instance. On the other hand, we constantly see breaches involving hosted systems, outsourced management, rogue vendors, and even VMs (though the attack vectors have nothing to do with it being a VM or not). In other words, it’s more about giving up control of our assets and data (and not controlling the associated risk) than any technology specific to the Cloud.”
So this paragraph is used to say that Cloud Computing is not a risk. It is secure. It can be trusted.
No wonder all the cloud providers have this paragraph in all of their PowerPoint decks now, something I’ll come back to in the future.
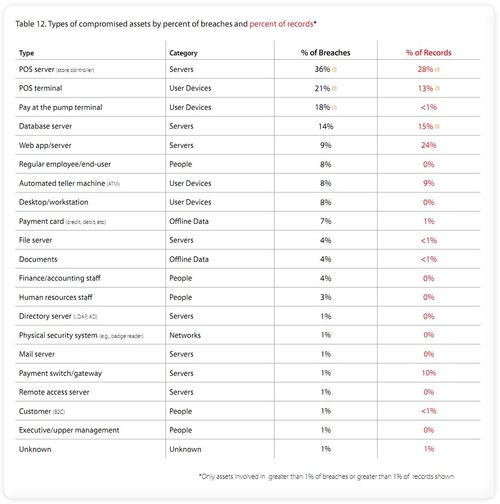
However, it may be more important to note that of the 761 data breaches Verizon examined in 2010, equivalent to nearly the whole number that occurred between 2004 and 2009, most were attacking retail hospitality and financial services.
This chart explains why (double click image to see chart clearly) …

… in other words, you wanna get money? The easiest place to compromise is a merchants’ terminal.
I guess that’s what makes the Merchant Risk Council, the Antiphishing Working Group, the National Anti Fraud Network, the Payments Council, the Serious Organised Crime Agency and others important.
These are all groups coming from different directions – government, police, retailers, financial services, regulators – to try to lockdown the fraudsters.
It’s a tough job though, as there are so many points of leakage.
Five billion and growing.
HT to Kamran Meer, Chief Information Security Officer at Habib Bank, for his references and support in writing this article.
The next meeting of the Financial Services Club, London takes place at Speechly Bircham's Conference Centre, 6 New Street Square, London EC4A 3LX from 6.00 p.m. on Thursday 9th June 2011.
The subject will be: Technology Trends: Fraud and Risk, and Mobile Device Insecurity
This Meeting will be based on two presentations.
How SOCA tackles organised crime with Andy Baker, Deputy Director, SOCA
Andy will outline SOCA’s approach to tackling organised crime in the field of financial technology. He will look at intellectual property crime (IPC), cybercrime and fraud, and take you through how this Executive Non-Departmental Public Body (NDPB) of the Home Office is working to prevent and solve these crimes.
Fraud and Risk, and Mobile Device Insecurity with Joshua Pennell of ISSA UK
They watch you sleep, they watch you work, they hold all your personal and professional data, and they sacrifice security for performance and usability. Your mobile devices present attackers with a 24/7 threat surface (and don't think the hackers haven't noticed). This presentation will dive into the world of mobile device security based on research performed by the IOActive team. It will address common threats, ways to better protect devices and show a demo of an attack in the wild.
If you wish to attend please register as follows: Member or Non-Member
Chris M Skinner
Chris Skinner is best known as an independent commentator on the financial markets through his blog, TheFinanser.com, as author of the bestselling book Digital Bank, and Chair of the European networking forum the Financial Services Club. He has been voted one of the most influential people in banking by The Financial Brand (as well as one of the best blogs), a FinTech Titan (Next Bank), one of the Fintech Leaders you need to follow (City AM, Deluxe and Jax Finance), as well as one of the Top 40 most influential people in financial technology by the Wall Street Journal's Financial News. To learn more click here...

